By Christopher Buse
May 19, 2021
 If you ask my wife Beth, what is love? She would say that love is like the two of us walking down a quiet beach at night under the moonlight. But to me, love is all about sitting on a northern Minnesota lake with my friends catching walleyes and drinking some refreshing pale ales.
If you ask my wife Beth, what is love? She would say that love is like the two of us walking down a quiet beach at night under the moonlight. But to me, love is all about sitting on a northern Minnesota lake with my friends catching walleyes and drinking some refreshing pale ales.
Over my career as an IT security professional and a CPA, it became clear to me that risk assessments are a lot like love. The term means something different to everybody. Absent a generally accepted definition, in this article I will describe where I landed in my career-long quest to better understand and manage risk.
I use four distinct lenses to view cybersecurity risk:
Cybersecurity Framework Lens. By mapping controls to a generally accepted framework such as NIST 800-53, I can measure whether our program aligns with industry best practices. In my most recent assessment, my team did a full NIST control mapping with IT leaders to garner buy-in of security controls and identify areas for improvement.
Regulatory Lens. Like it or not, we all operate under a regulatory microscope. Therefore, it is important to map IT security controls against regulatory provisions to assess the potential risk of noncompliance.
Threat Lens. Anticipating the latest threat vectors is always a crapshoot. Nonetheless, it is prudent to take the time to formally map controls against major threat trends, such as ransomware.
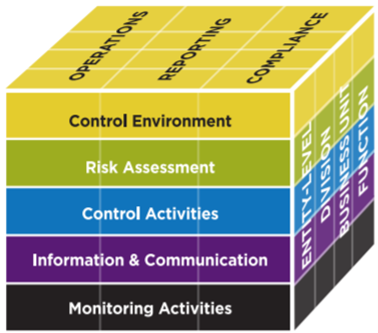 Control Environment Lens. High profile frauds which lead to the collapse of Enron and other organizations taught us lessons about the value of a robust control environment. In fact, based on recommendations from the Committee of Sponsoring Organizations of the Treadway Commission (COSO), a control environment assessment is now a required part of all financial audits. This concept is equally applicable to IT security risk assessments. Areas to consider evaluating are program funding, risk bar clarity, and governance effectiveness, just to name a few.
Control Environment Lens. High profile frauds which lead to the collapse of Enron and other organizations taught us lessons about the value of a robust control environment. In fact, based on recommendations from the Committee of Sponsoring Organizations of the Treadway Commission (COSO), a control environment assessment is now a required part of all financial audits. This concept is equally applicable to IT security risk assessments. Areas to consider evaluating are program funding, risk bar clarity, and governance effectiveness, just to name a few.
Many organizations conduct an IT security risk assessment because they are required to do so. However, organizations that conduct risk assessments to check a compliance box will undoubtedly fail to realize some important benefits. When done thoughtfully, IT security risk assessments help stakeholders understand their true cybersecurity risk posture. Key stakeholders include IT leaders, IT security leaders, and executives, who are the ultimate owners of risk. IT security risk assessments also help fuel important conversations about where to set the risk bar in policies and standards. And arguably most important, risk assessment results help drive strategic and tactical efforts to address cybersecurity program gaps.
Much like with life and with love, a comprehensive risk assessment cannot guarantee that bad events will not happen. In 2017, my wife was diagnosed with stage four cancer and we were told that we most likely had a year left together. I immediately resigned from my CISO role and we embarked on a journey to travel and make memories. Fortunately, it has now been over four years since our devastating cancer prognosis and our family is intact and doing well. Nobody knows for certain, but I believe that significant lifestyle and diet changes helped us manage our newfound cancer risk.
I am happy to report that I am back in the cybersecurity profession, and I am looking forward to meeting all of you at the upcoming Cybersecurity Summit, this October 25-27. I also am excited to report that this month I will be heading up to northern Minnesota with my friends for the fishing opener. But I do need to let you in on a little secret that I learned over the past four years on our cancer journey: love is in fact strolling down the beach at night with my beautiful wife.
 A lifelong finance and IT security professional, Christopher Buse serves as CISO for Old Republic Title Insurance Company. Prior to this, Christopher served as the first CISO for the State of Minnesota and as Deputy Legislative Auditor for the Minnesota Office of the Legislative Auditor. Christopher has been active in numerous professional organizations, sector-based ISACS, and was one of the founding members of the Minnesota Cybersecurity Summit. » Read full bio
A lifelong finance and IT security professional, Christopher Buse serves as CISO for Old Republic Title Insurance Company. Prior to this, Christopher served as the first CISO for the State of Minnesota and as Deputy Legislative Auditor for the Minnesota Office of the Legislative Auditor. Christopher has been active in numerous professional organizations, sector-based ISACS, and was one of the founding members of the Minnesota Cybersecurity Summit. » Read full bio
