4.24.23 > Matt Hoyland for Island
“Sometimes changing one thing changes everything. The Browser is the Enterprises most used application, but Browser’s traditional focus has been for Advertisements and Content Delivery. Our friends at Island reimagine the Browser to give Enterprises full control of their data and how it interacts with other applications. The TAG Cyber team recently took a look at the Enterprise Browser, and makes a very compelling case on why it should be included in compliance frameworks.”
This note introduces a set of cybersecurity requirements that should be integrated into the browser and included in major compliance frameworks to counter common cyber risks to corporate enterprise users.
Prepared by Ed Amoroso, TAG Cyber, Version 1.0, March 18, 2023
Introduction
It’s surprising that with so many different advanced cybersecurity tools, platforms, features, and methodologies, that relatively light attention has been placed on the central role of the browser in most on-line applications and sessions. Any cursory glance at the typical security relevant situation involving human users reveals how the browser generally resides in the middle of access requests, session initiation, data sharing, and so on.
This brief note outlines the cybersecurity features we recommend for inclusion in the enterprise browser to deal with emerging cyber risks – including from increased use of artificial intelligence in browsing and search. We believe that proactively demanding these protection capabilities is a wise for enterprise. The good news is that commercial vendors are available today for enterprise security teams who desire these features.
Cyber Risks Involved in Browsing
It helps to review the various cyber risks that emerge with respect to browsing. These include malicious exploitation in browser vulnerabilities or poorly selected configuration choices by users. The good news is that best practices have emerged for patching and optimizing browser configurations, especially in enterprise settings with capable IT security staff. But browsers are still soft spots for malicious entities trying to achieve the following types of hacks:
- Obtaining Information – This is usually helpful in a phishing scenario where the browser might offer guidance on behavioral patterns, sites visited (from histories), and purchasing habits. The browser can offer a window into targeted victim, so it is obviously an important resource to protect.
- Exploring Saved Data – This involves login credentials (often to banking websites), autofill information, cookies, and other personalized data. Again, the good news is that IT security teams have been successful in helping employees manage their browser in a reasonably secure configuration (e.g., including with URL filtering to avoid inappropriate websites).
The impact of AI-enabled browsing will offer a significantly improved user experience for finding information, personalizing search, and automating various activities and tasks. For example, the introduction of OpenAI’s ChatGPT to the Microsoft browsing experience illustrates this intriguing new capability. Google is also working hard to enhance the browsing functionality with chatbot functions.
The full cybersecurity implication of AI-enabled browsing will not be known until this capability is deployed at scale. In advance of this shift, it is prudent for enterprise security teams to take preventive action to avoid threats that are predictable (such as the examples cited above) and perhaps less predictable. The section below suggests that security-enhanced browsers will be an important part of the protection equation.
Benefits of Security-Enhanced Browsers
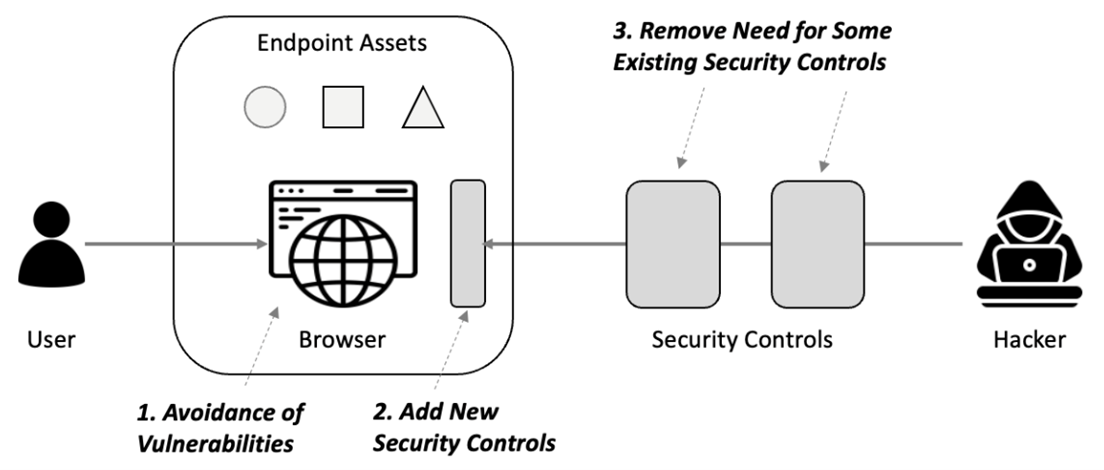
Broad security requirements for enterprise browsers come in three categories. First, browsers should be free from vulnerabilities. This has been an especially nagging issue since self-propagating malware could no longer rely on open access to target networks through open ports on the firewall. Entry points required exploitable vulnerabilities, so browsers became popular targets. This must therefore be prevented.
Second, browsers should be designed to provide reasonable options for individuals or organizations to either remove or avoid use of as many existing comparable tools as possible. Consider, for example, that endpoint security has emerged as one of the most expensive line-items for IT and security teams. As such, if the browser can offer cheaper alternatives consistent with budget (or lack thereof), then this is desirable.
Finally, browsers should provide so-called last-mile protection for the end-user. This makes particular sense because the browser provides the most direct interface between the user any applications being accessed. If malware finds its way through the typical gauntlet of controls that exists between a web application and a user, then the browser should provide a final safety net to protect local resources.
Figure 1. Security Roles for the Browser
The implication of last-mile browser defense is that pre-integration is recommended with existing PC and device controls such as endpoint detection and response (EDR), content disarm and reconstruction (CDR), and anti-malware security software. The business opportunities are significant for vendors, certainly – but the real value will come from enterprise teams who will experience better endpoint security.
Proposed Inclusion in Frameworks
A significant issue in modern cybersecurity is that the existing popular frameworks dictating the protection control architecture for most enterprise teams are largely silent on last-mile browser security capabilities. This creates a gap in many programs, especially ones that are highly influenced by formal frameworks, including in highly regulated industries such as financial services, utilities, and telecommunications.
A review of existing popular frameworks,[1] including the NIST Cybersecurity Framework (CSF), Payment Card Industry (PCI) Data Security Standard (DSS), International Standards Organization (ISO) 27000 series confirms this last-mile gap. None of the frameworks includes, for example, copy-and-paste controls for the browser – and some barely scratch the surface of browser-based controls.
One excellent resource for information on browser security controls is the Chromium Security website maintained as part of The Chromium Projects.[2] The Chromium security team provides users of its open source (which is the basis for most enterprise offerings) with security features consistent with the following principles: Help users safely navigate the web, design for defense in depth, security is a team responsibility, speed matters, and be transparent.
Given such excellent resources, our TAG Cyber analyst team urges the purveyors of security frameworks and any other stakeholders, to begin the process to address the standards gap. We believe that a set of simple requirements can be defined that will fit well into modern compliance frameworks. Even if enterprise teams opt to not address these requirements, their inclusion will increase awareness and help promote use where it will be most important.
The specific last-mile browser security requirements we recommend for inclusion in frameworks such as NIST 800-53 and PCI-DSS are summarized below:
- Data Management – The browser should include functional controls for where and when users can copy and paste data into or out of applications.
- Device Posture – The browser should include means for confirming that device security status is acceptable before granting access.
- Screen Capture – The browser should manage whether requested screen captures are allowed or authorized.
- Browser Extensions – The browser should include controls for which extensions are considered acceptable for installation.
- Workflow Support – The browser should include functional integration with applicable workflow tools in the enterprise.
- Data Storage – The browser should include controls for how data is stored and under what types of conditions.
- Geographical Controls – The browser should use location as the basis for geo-fencing controls required by an enterprise.
Readers are urged to consider improvements to the list presented above – and framework curators will likely have opinions about improved wording, references, and other means for presenting the new control statements. Regardless of the implementation process, we hope that last-mile browser security controls are taken more seriously in the industry, and that this is codified in our major security frameworks.
[1] This technical review was performed in late 3Q22 by members of the TAG Data Research (TDR) team within TAG Cyber including Iassen Christov, Carlier Hernandez, Shawn Hopkins, Khanjan Patel, and Nick Wainwright. [2] https://www.chromium.org/Home/chromium-security/ [1] This technical review was performed in late 3Q22 by members of the TAG Data Research (TDR) team within TAG Cyber including Iassen Christov, Carlier Hernandez, Shawn Hopkins, Khanjan Patel, and Nick Wainwright. [1] https://www.chromium.org/Home/chromium-security/
TAG Cyber is a trusted cyber security research analyst firm, providing unbiased industry insights and recommendations to security solution providers and Fortune 500 enterprises.
Copyright © 2023 TAG Cyber LLC. This report may not be reproduced, distributed, or shared without TAG Cyber’s written permission. The material in this report is comprised of the opinions of the TAG Cyber analysts and is not to be interpreted as consisting of factual assertions. All warranties regarding the correctness, usefulness, accuracy, or completeness of this report are disclaimed herein.
You can Connect with Matt Hoyland on Linkedin at https://www.linkedin.com/in/matthoyland/
And you can learn more about Island and the Enterprise Browser
What if the enterprise had complete control over the browser?
What would it do for security, productivity, for work itself?