 |
 |
Basic Threat Modeling and Risk Assessment Fotios Chantzis |
What are the chances? Lessons learned from 50 years of predicting risk. Douglas Clare |
 |
Why Security needs to be at the DevOps Table Chris Perkins |
 |
 |
5 Steps Toward GDPR Compliancy in Practice Pekka Vepsäläinen |
Information Security Best Practices and GDPR Douglas Garrison |
 |
 |
Communication Strategies and Lessons Learned Loren Dealy Mahler |
Industry Standard Frameworks: What You Need to Know and How to Use Them Amos Aesoph |
 |
The Top 10 Things You Must Do to Protect Security Systems from Cyber Attacks David Tyson |
 |
 |
 |
The Anatomy of an Email-Borne Attack Brandon Reid |
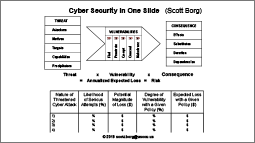
Economics of Cybersecurity Scott Borg |
Legislative Cyber Security Briefing: IT Security Governance Tony Sager |